Description
The Understanding the Anatomy of a Cyber Attack PowerPoint Presentation is a comprehensive and informative tool designed to educate audiences on the various components and stages of a cyber attack. This visually engaging presentation delves into the different methods and techniques used by cyber criminals to infiltrate systems, steal data, and wreak havoc on businesses and organizations.
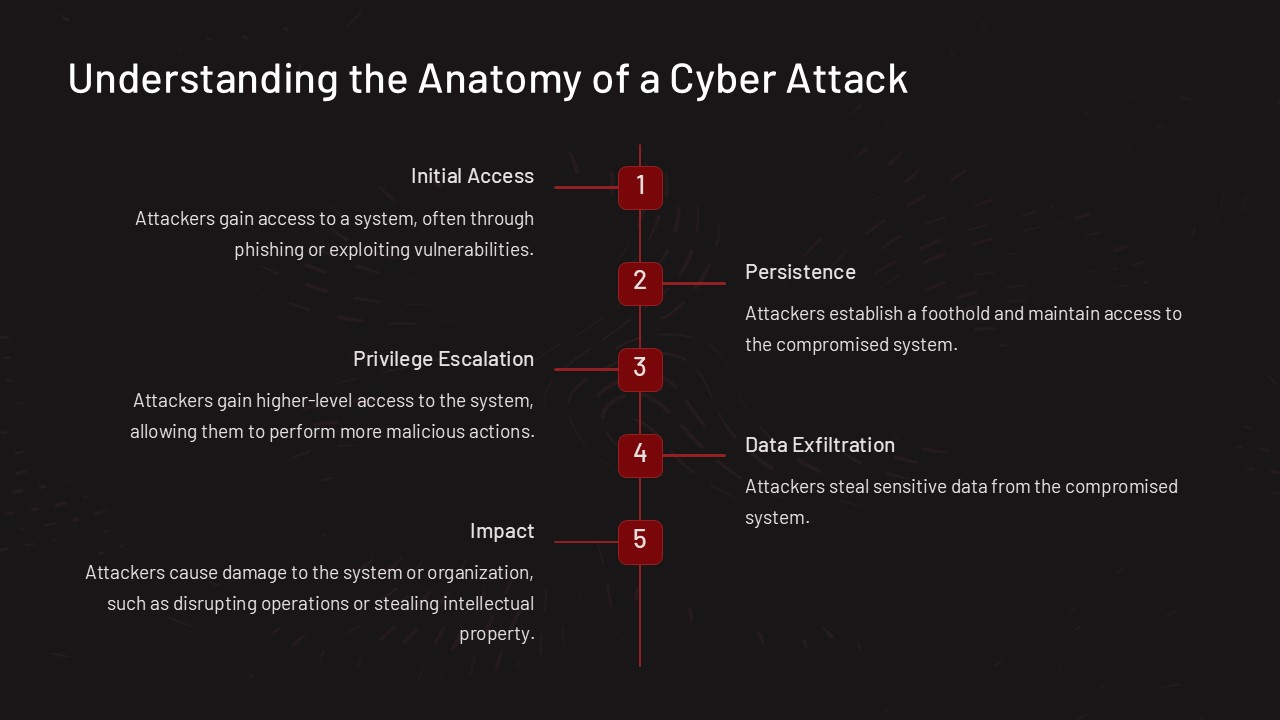
With detailed slides that break down the anatomy of a cyber attack step by step, this PowerPoint presentation is an invaluable resource for cybersecurity professionals, IT teams, and anyone looking to enhance their knowledge of digital threats. From initial reconnaissance and weaponization to delivery, exploitation, installation, command and control, and actions on objectives, each stage of a cyber attack is thoroughly explained and illustrated to help viewers better understand the complexities involved in safeguarding against such threats.
Key features of the Understanding the Anatomy of a Cyber Attack PowerPoint Presentation include:
1. Fully editable slides: Easily customize the content, colors, and graphics to suit your specific needs and preferences.
2. High-quality visuals: Professionally designed graphics and diagrams enhance the presentation and make complex concepts easier to grasp.
3. Comprehensive content: Covering every aspect of a cyber attack, this presentation offers a detailed overview that is both informative and engaging.
4. Versatile use: Suitable for training sessions, workshops, seminars, and educational purposes, this PowerPoint presentation can be adapted for various settings.
5. Updated information: Stay informed on the latest trends and tactics in cyber attacks with content that is regularly reviewed and updated to reflect current threats.
Overall, the Understanding the Anatomy of a Cyber Attack PowerPoint Presentation is a must-have tool for anyone looking to increase their understanding of cybersecurity threats and protect their assets from potential breaches. With its user-friendly design and comprehensive content, this presentation is sure to be a valuable asset in your cybersecurity arsenal.










There are no reviews yet.